Trezor.io/start — Set Up & Secure Your Trezor Wallet
Official step-by-step instructions to unbox, initialize, and operate your Trezor hardware wallet safely — including setup with Trezor Suite and essential security practices.
Welcome — Why Start at Trezor.io/start?
Trezor.io/start is the official starting point for anyone new to Trezor hardware wallets. The page consolidates verified download links, setup tutorials, and security tips so you can get your device up and running without falling prey to phishing or counterfeit products. Starting here ensures you follow the manufacturer-recommended flow: download Trezor Suite, initialize the device, and record your recovery seed correctly.
Unboxing & Initial Inspection
When your Trezor arrives, inspect the packaging carefully. Factory seals should be intact. If anything looks tampered with, do not use the device and contact official support. Inside the box you’ll usually find the Trezor device, a USB cable, recovery seed cards, stickers, and a short manual. Do not initialize the device if it arrived with a pre-populated recovery phrase or PIN.
Download Trezor Suite
Trezor Suite is the official desktop (Windows, macOS, Linux) and web application to manage your Trezor wallet. Visit Trezor.io/start and follow the secure download links. After downloading, verify the installer if you can — many users skip this, but it adds a layer of safety against tampered installers.
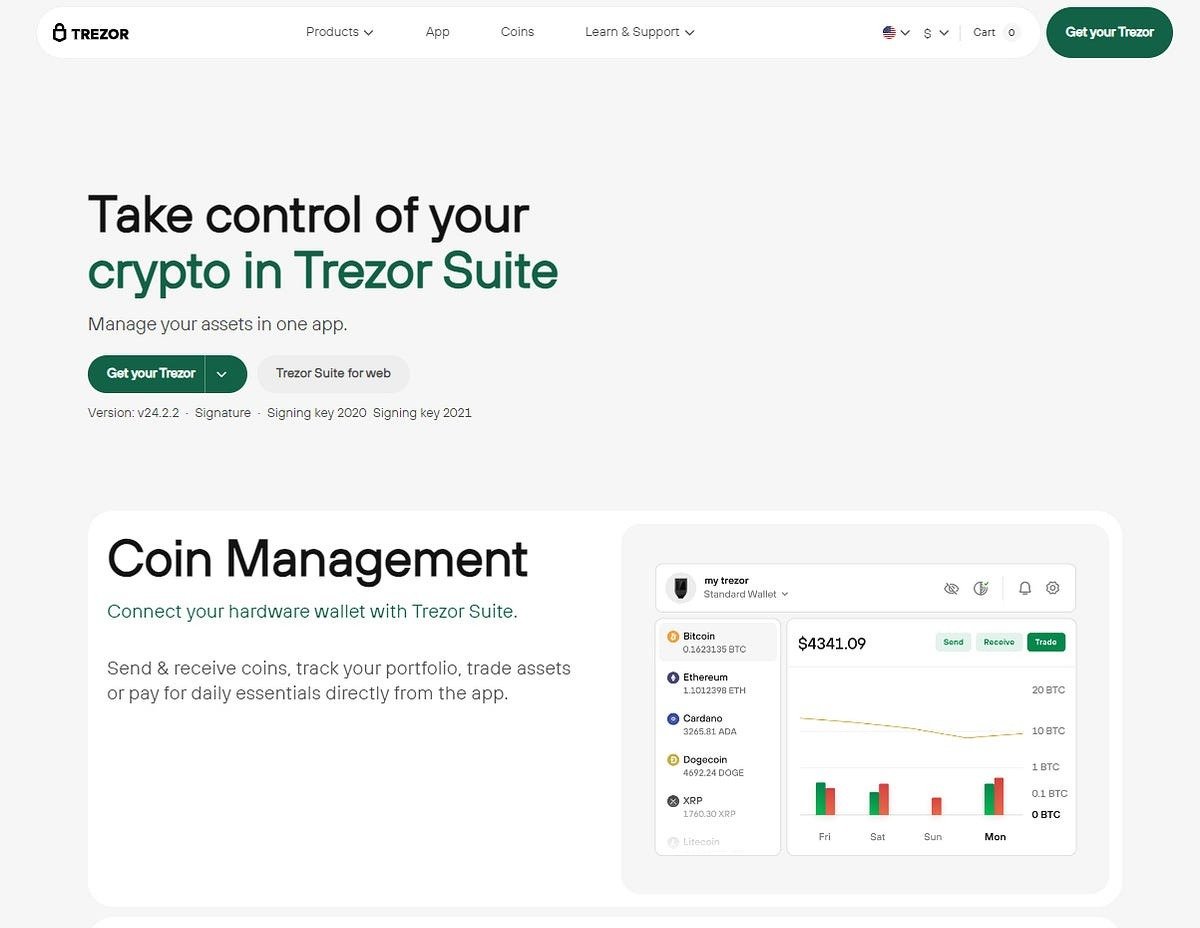
Initialize Your Trezor
- Connect: Plug the Trezor into your computer using the provided cable and open Trezor Suite.
- Create or recover: Choose between creating a new wallet or recovering an existing seed.
- Create: Trezor will generate a new 12–24 word recovery seed on the device.
- Recover: Enter your existing recovery seed on the device only if you are restoring.
- Record the seed: Write down each recovery word on the physical recovery cards provided. Store these cards offline in a secure place — consider multiple copies or a metal backup for long-term durability.
- Set a PIN: Choose a PIN that you can remember but is not easily guessable. The PIN protects the device if it is lost or stolen.
Security note
Never type your recovery seed into a computer, phone, or cloud service. The seed belongs only on the device and on securely stored offline media.
Understanding Passphrase & Hidden Wallets
Trezor supports an optional passphrase feature which creates hidden wallets derived from your seed. This adds plausible deniability and extra security, but it also adds complexity: if you lose the passphrase, you lose access to those funds. Use passphrases only if you understand the tradeoffs and can store the passphrase securely offline.
Daily Use — Sending and Receiving Crypto
Trezor Suite provides a clear interface to receive and send cryptocurrencies. Always validate the receiving address displayed in Trezor Suite against the address shown on your Trezor device screen — the device is the source of truth and prevents address substitution attacks.
- Open the account you want to use in Trezor Suite.
- Click Receive to generate an address; verify it on the device screen.
- To send, build the transaction, check fees, and confirm the details on your Trezor device before approving.
Firmware Updates
Keep your device firmware up to date. Trezor Suite will prompt you when updates are available. Firmware updates can include critical security fixes and new coin support. Follow the on-screen instructions carefully and avoid interrupting the device during an update.
Troubleshooting Common Issues
- Device not recognized: Try a different cable/USB port or restart Trezor Suite.
- Seed recovery problems: Ensure you are entering words exactly as written, with correct spelling and order.
- Firmware update failed: Reconnect the device and retry; consult official support if issues persist.
Best Practices for Long-Term Security
- Store recovery seeds in multiple secure offline locations; consider fireproof and waterproof storage.
- Use a unique PIN and consider passphrase usage only if necessary.
- Keep Trezor Suite and firmware updated through official channels.
- Avoid entering recovery data anywhere other than the device itself.
Privacy Considerations
Blockchain transactions are public. Use separate accounts, avoid address reuse, and consider privacy-focused coins or mixing techniques where legal. Trezor helps by providing local address management, but privacy ultimately depends on how you use the blockchain.
Conclusion
Starting your Trezor journey at trezor.io/start gives you the safest and most reliable path to securing your cryptocurrencies. From secure downloads and guided initialization to best practices for backups and daily usage — following the official flow reduces risk and keeps your assets protected. Treat your recovery seed as your most valuable asset and store it offline, verify everything on-device, and keep your firmware and software current.
Visit trezor.io/start to begin — secure your crypto with confidence.